By
Apryl Motley - Technical Writer & Communications Lead, Internet2 Trust and Identity/NET+ Service
Estimated reading time: 2 minutes
According to Stony Brook researchers Nick Nikiforakis and Babak Amin Azad, research and education institutions can defend against phishing attacks that leverage man-in-the-middle (MITM) phishing toolkits acting as malicious reverse proxy servers of online services.
Last month during a NET+ I2 Online webinar, “Mitigating MITM Phishing Toolkit Attacks that Bypass MFA,” they presented the findings from a year-long analysis of MITM phishing toolkits they conducted in collaboration with a researcher at NET+ service provider Palo Alto Networks. By analyzing and experimenting with MITM phishing toolkits, they identified intrinsic network-level properties campuses can use to identify and defend against them. (Watch the recording now.)
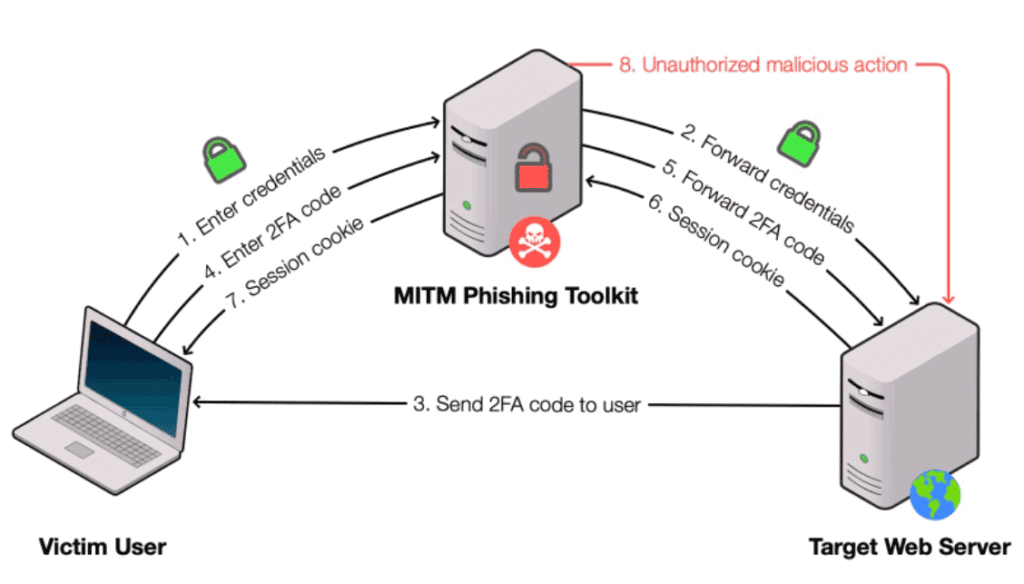
The diagram above outlines how these attacks work.
NET+ Program Manager Nick Lewis moderated this important discussion. “Having talked with a number of campus information security teams over the last six months to a year, I know a number of campuses have experienced these types of attacks, but overall awareness of them has been pretty uneven,” Lewis said. “We were fortunate to have two Stony Brook research team members address the community to improve our awareness and better understand how this emerging threat impacts higher education.”
“I firmly believe in raising awareness about the presence of these toolkits,” Nikiforakis said. “Just because you log in and see your emails in your inbox or just because you’re using two-factor authentication, that doesn’t mean that you’re secure. You should still be aware that these attacks can happen, which may help you identify that something odd is going on.”
If you missed it, don’t worry! You can still benefit from the insights shared on effectively addressing this emerging threat and hear your peers’ questions about managing it on their campuses.
Once again, we thank Carahsoft Technology Corp for sponsoring this event. Visit them at www.carahsoft.com.
About the Author(s)
Apryl Motley
amotley@internet2.edu
Technical Writer & Communications Lead, Internet2 Trust and Identity/NET+ Service
Apryl Motley, CAE, leads communications efforts for the Trust and Identity and NET+ teams at Internet2, including content development for their respective newsletters. Apryl has been working in the communications field for more than two decades.